When you purchase something precious, like gold, jewellery, a house or something equally expensive and ostentatious, you take good care of it. You make sure that it is insured and that it is safe and protected in every way possible.
Similarly, when a business owner starts up and new business, it makes perfect sense for him to purchase new equipment of all sorts that the business would need. The business owner also hires some of the best minds in the field to ensure that the business blooms and prospers.
Learn About Spyware In These 5 Simple Points
Spyware is using software for spying over someone’s PC or devices. Once spyware is installed you can see performance of your computer drop. The main symptom
Now, it is hard to find a business owner that has spent quite some time and effort along with a significant amount of money in his business would let it all go to waste without safeguarding his property. Even from an economic standpoint it seems like an extremely foolish thing to do so.
Therefore, it makes perfect sense to a layman that a business owner or employee has installed trackers, bugs and spy application onto the office and why wouldn’t they?
It seems like quite the reasonable thing to do in light of all the ways employees exploit office hardware and internet. But, the question that stems from this is about the legality of the matter, whether employees are allowed to install trackers, bugs, spy apps on office hardware and similar equipment.
How Your PC Can Be Spied On Through Your Keyboard Keystrokes
There are times when for some reason we need to know what is going on with our PC, like what sites are being accessed or just if our keyboard keystrokes are being tracked
Is Bugging Office Hardware Even Legal?
Since business owners are the one to purchase the office equipment used by the employees in the first place, this means that employees have no ownership right over the equipment whether they bring it home with them or leave it on their office desk.
As all such equipment legally belongs to employees and business owners, they have sole ownership and responsibility of all such equipment. Therefore, they are perfectly authorized by the law to do as they please with the office equipment that falls under their ownership.
Additionally, more often than not, companies do place protective bugs and trackers on such equipment to keep track of them at all times especially if they have a mobile workforce working for them.
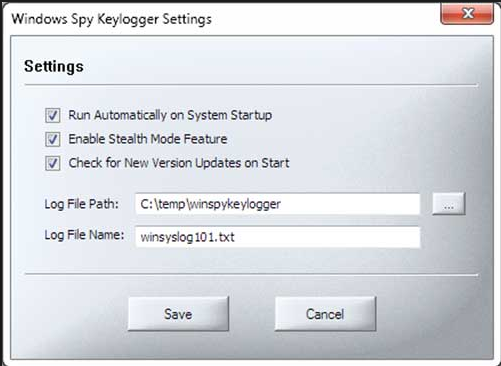
Monitor The Activity Of Your Windows 10 With This Keylogger
A Keylogger is an application that installs and hides in the system in order to monitor all activity that takes place in the windows operating system. Based on the
Benefits of Bugging – Bugs and Trackers
Bugs, trackers and spy applications are indeed a brilliant invention. Not only because it gives business owners more control over their work-space but also because of various other benefits it has, such as:
1. Control your Workspace
More often than not, productivity in a workspace always lags behind the expected quotient, not because the company has way more projects than it can handle but, because employees would rather spend all their time texting their co-workers, watching funny videos online or aimlessly surfing the web rather than actually doing something productive.
Such behavior not only reflects badly on the company, but it reduces the monthly revenue of a company significantly.
Spy apps and trackers can easily remedy this situation since they allow employers to keep a keen digital eye on their employees and ensure that they are doing what they are actually being paid to do.
4 Important Tips To Avoid Spyware From Disturbing You
Spyware refers to software that is installed on a computer without the user’s knowledge. It can be used to track and monitor the user activities to avoid Spyware
2. Keep Mobile Workforce in Line
Most spy apps like the TheOneSpy are equipped with both bugs and trackers. Plus, they work brilliantly if your business needs you to employee a mobile workforce.
Ever since the inception of this concept, keeping mobile workforce in line has been a hell of a task. Since they have to work onsite and away from the workspace, they tend to get countless opportunities pull wool over the employer’s eye by slacking off and taking too long to do a mental job.
With spy apps in the mix, the chances of them slacking off and running personal errands is greatly reduced since business owners can easily catch their bluff, thanks to trackers and spy apps.
3. Keep Internet Abuse at Bay
Another benefit of keeping an eye on company hardware is the millions of dollars a company can potentially save by keeping employees from having unlimited access to the internet.
Since, employees waste most of their hours at the office doing non-work related web services, it can take a serious toll on both the productivity of an employee and the monthly revenue it makes.
With the use of spy apps, business owners can not only keep track of employee’s internet usage but also reduce it significantly but limiting employee access to it.
Erase All Traces Of Your Activity In A Click & Stay Secured
One of our biggest worry is to preserve the privacy and security of our Internet browsing. This Browser cleaner Erases All Traces Of Your Activity With Just A Small Click