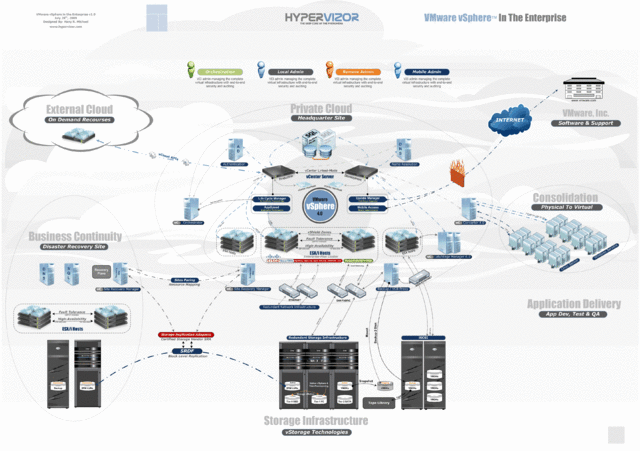
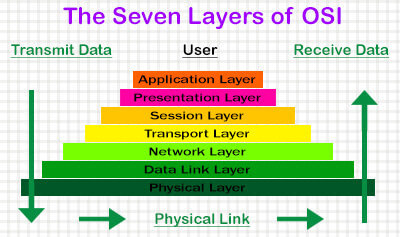
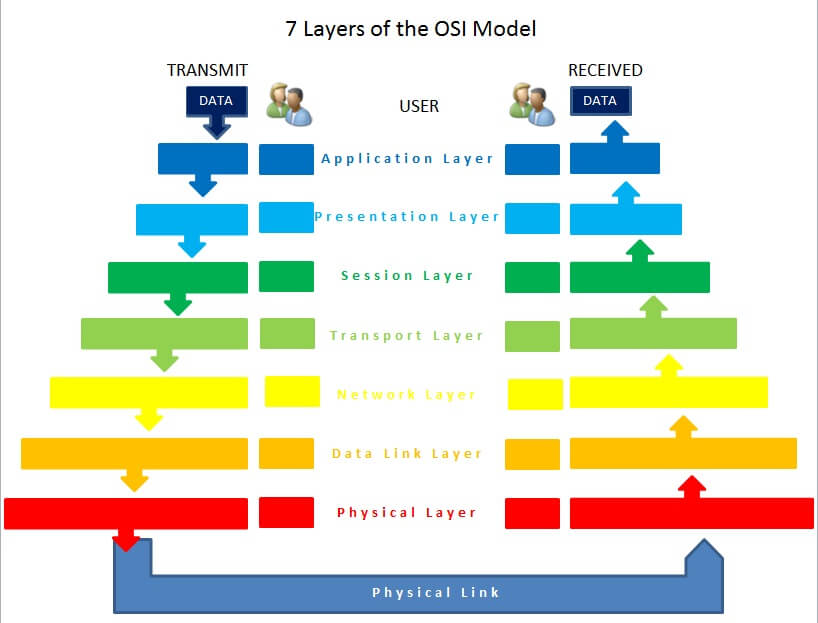
Cloud computing has very fast evolved into a basic methodology for building IT structures and services. The number of companies opting for cloud deployment has been rapidly increasing; proving that the cloud isn’t just a technology. However, cloud computing is classified based on cloud location or services offered.
Image Credits: Mashable
In this article we will take you through the difference the various types of cloud have in them based on the cloud location. You can find the differences in clouds based on services they offer here – IaaS, SaaS, PaaS are the fundamental models of cloud services.
Different Types of Cloud
Public Cloud:
In a Public Cloud, the entire computing infrastructure is provided to the general public by a service provider, who hosts the entire infrastructure. However, there would absolutely be no control over the infrastructure on part of the customer. These service providers are companies which hold data of customers and this data is available for the customers on the Internet.
In a nutshell, customers have no control or rights over the infrastructure location or maintenance. Also since all customers on the public cloud share common infrastructure with limited configuration there are several advantages and disadvantages associated with this public cloud model which will be listed in some other article later on.
Also Read: The Ultimate Cloud Data Security Mantras For Individuals and Businesses
Private Cloud:
In the private cloud model, the infrastructure is all in the hands of one particular organization. The control and visibility that’s lacking in public clouds is with businesses within this cloud model. The private cloud is implemented within the enterprise firewall and can also be remotely located from the enterprise.
Since there is no sharing of infrastructure with others, the security risks are minimal. With a private cloud there’s more security and more expenses.
Also Read: A Personal Private Cloud In Your Home Isn’t A Bad Idea
Hybrid Cloud:
The Hybrid Cloud model is simply the combination of both public and private clouds. Suitable cloud model is utilized based on purpose. Hence costs are reduced without compromising on security. Many organizations follow this trend in hosting critical applications and the relatively less important applications are hosted on the public cloud.
The only downside is in keeping track of all the cloud security platforms and managing them properly for them to communicate with each other effectively.
Also Read: Difference between Cloud Computing and Virtualisation
Also Read: Differences between Managed Cloud and Unmanaged cloud