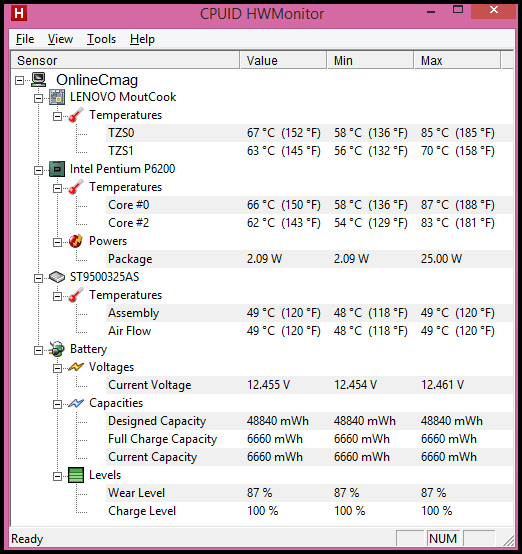
One of the most important changes that we can make in our computer to increase the potency is overclocking. Overclocking is a process to increase the frequency of processing of our microprocessor at higher levels than the default, i.e simply asking our microprocessor to work harder.
Before going into detail about this practice, we should note that the increase in microprocessor performance is not enabled on computers that are manufactured under one brand and specific model.
Since they come protected against this overclocking, this operation is mostly performed on computers that have been assembled by third-party equipment.
Overclocking is making your computer’s hardware run much faster than what they are designed for by manufacturers. If you are thinking about it, you can actually do
Read More
We also recall that this practice without sufficient knowledge can cause hardware damage and possibly alter the factory settings of these elements, which will result in immediate loss of warranty. Therefore make these practices under your full responsibility.
What Exactly Is Overclocking?
Overclocking is mostly described as the method which aims to achieve a higher clock speed, which is always above the manufacturer’s specifications and their standard values. This practice has one goal i.e to achieve higher performance from the components for free.
Overclocking is a term used in computing which means literally on the clock, i.e the clock frequency increase, which will increase processing capacity. You can have a detailed look about this Overclocking in our previous article.
What are its Pros and Cons?
On the pro side, obviously we can increase the capacity of our microprocessor for free and without hardly having to make any adjustments, and it is also a fast process.
On the downside, firstly the warranty of the device is totally lost as you alter the default condition of the component and it will also have changes in its stability, heat gain and possible reduction in life.
In case you don’t want stuff like this to happen to your computer, you can always quit this idea.
How can you Overclock?
If you’ve already decided to do so, you should know that there are two ways to overclock your system. Both of them are pretty easy to implement, they are as follows.
Methods To Increase The Power Of Your Computer
Method 1:
Through the BIOS: This is the cleanest and the most optimal and the highly recommended way to Overclock.
You just only need to access the BIOS your computer and Move on to the reference voltages and frequencies section.
Be very careful while modifying the values, If you have given a value which is considered to be very large than the value that your components can handle then it may lead to the hardware damage.
Occasionally, we may find that our computer suffers hardware problems that we don’t understand and do not know how to solve but have you tried getting over the issue by clearing the CMOS memory?
Read More
You must be very clear about the information being shown in your BIOS and what you should change, one should definitely research before making the change.
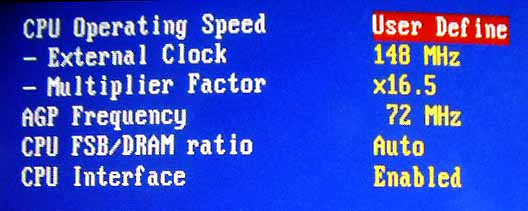
Method 2:
Through software: There are far many applications in the market to modify the default values of your computer in order to overclock.
Such applications are compatible with most devices and their use is often simpler than the method of the BIOS.
This method requires your BIOS password to be disabled ( i.e your computer should not have any BIOS password), of course, it will run only in administrator mode.
The operation is pretty simple you just need to restart your computer after making the changes. One of the simplest applications for this action is ” ClockGen “, Which can be download for free at the end of the article.
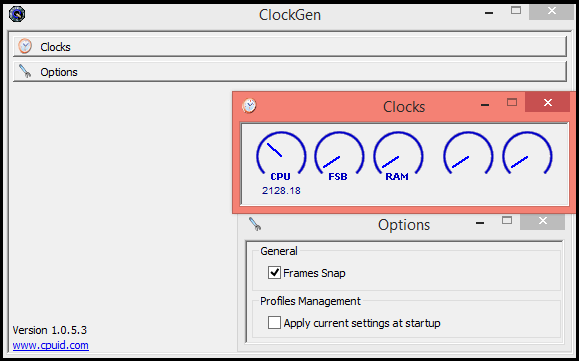
So, if at all you are thinking about modifying your computer to give it more power and speed, then you know what to do.
Softonic | ClockGen