Outlook users are always worried about the size of PST files that becomes corrupt whenever it reaches to its size limit. In earlier versions ANSI PST files only provide 2 GB storage limit, but upgraded versions increase this ability to 20 GB in Unicode PST files. Nevertheless, because of constant usage in corporate sectors, PST file size gets easily fulfilled causing worries to users. In such cases, extracting email attachments from PST file might help to keep your PST file size maintained. The main cause of the PST file increase is attachments, so in this upcoming segment we will be discussing about the Outlook Attachment Extractor tool that will help to extract email attachments from bulk Outlook PST files in one go.
Outlook Attachment Extractor
Integrated with advanced features, Outlook attachment extractor tool has the ability to remove email attachments from bulk Outlook PST files. Without damaging or hampering any other property of PST file the tool works to extract only attachments of all types like doc files, images, audio & video, etc. Users can add more than 100 PST files with tool at a time to extract the attachments, without facing any technicality the tool will obtain all attachments and save them to desirable location in local machine of the user.
Benefits Of Using Tool
- Remove attachments from bulk Outlook PST files
- Retain metadata and data file properties unchanged
- Maintain folder hierarchy of Outlook PST file attachments
- Works with both ANSI & Unicode PST files
- Remove attachments from PST file of any size
- Self-illustrative steps to carry out an email attachment process
Technical Specifications
To run the tool, MS Outlook 2013 any below version installation is mandatory in the user’s machine.Windows 8.1/8/7 and Vista users are required to run the tool as Administrator.There were no special system requirements of tool, some general specifications are required that are capable to handle by any system.
Basic Details About Tool
Size: 3.6 MB
Version: 2.0
Basic Function: Extract all Attachment from Outlook PST file
Trail Facility: Demo Version
Spyware and Malware free: Norton and McAfee secure
Microsoft Windows Support: 2000, 2003, 2008, XP, Vista, Windows 7/8/8.1
MS Outlook Versions: 2000, 2003, 2007, 2010 and 2013
Demo Version Conditions
The demo version of Outlook Attachments Extractor tool is available for users at free of cost. Users can download this trial version of tool in system without investing any money. The trail mode will help to extract first 20 attachments from 5 PST files and will provide a preview of how software works. Once the working and ability of tool is evaluated, users can make an investment in licensed version of tool from official website of organization.
Full Version Details
The full version of Outlook Attachment Extractor tool is available multiple licenses i.e. Personal, Business and Enterprise, to provide a users facility to extract attachments from bulk PST files. By investing in any of the licensed version of tool, users can grasp the facility of extracting Outlook attachments from multiple PST files without facing any limitations. The organization also provides extended support assistance and updates facility along with licensed version of tool.
Detailed Working Of Software – Illustrated
For obtaining positive results out of tool, it is necessary to handle the tool properly. So here we are helping you to with detailed manual of Outlook attachment Extractor tool, to attain perfect and desirable results.
- First download and install full version of the Outlook Attachment Extractor tool in your system and run it from Start > All Programs > Outlook Attachments Extractor.
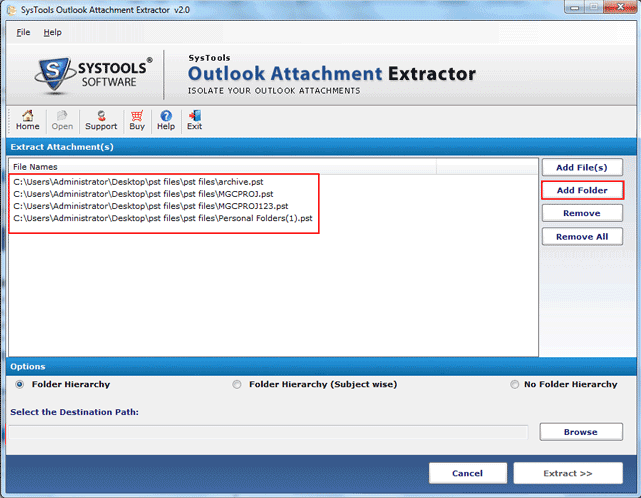
- From the initial screen of tool, user has to click on “Open” to start the process of Outlook attachment extraction.
- Now click either on “Add File” or “Add Folder” option to add Outlook PST files with tool to extract email attachments.
- “Remove” and “Remove All” options are also provided to remove accidently or unnecessary added PST files from tool interface.
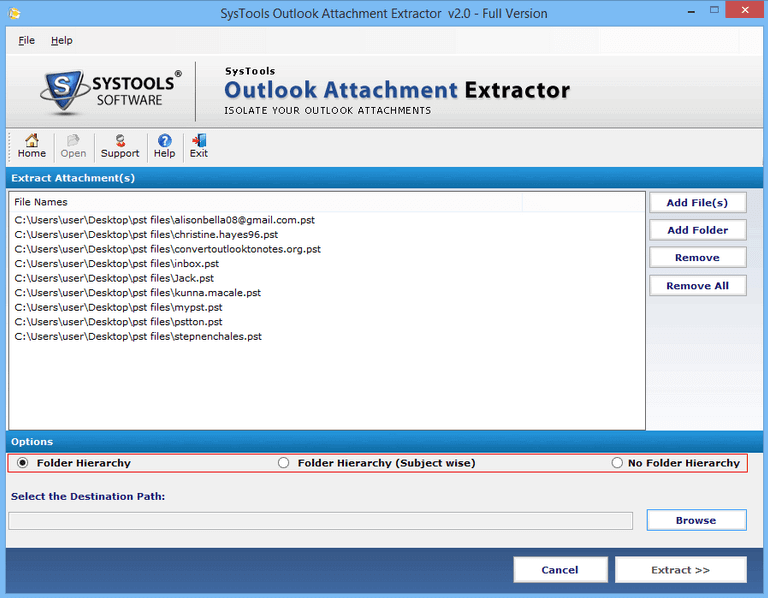
- There are three options i.e. Folder Hierarchy, Folder Hierarchy (Subject Wise) and No Folder Hierarchy, select as per your convenience and proceed to further step.
The folder hierarchy option is provided to extract and save all PST file attachments according to PST file hierarchy.
Folder Hierarchy (Subject wise) option is provided for users save all email attachments according to the subject of all emails.
Choose No Folder Hierarchy option to save all email attachments alternatively as per software ability.
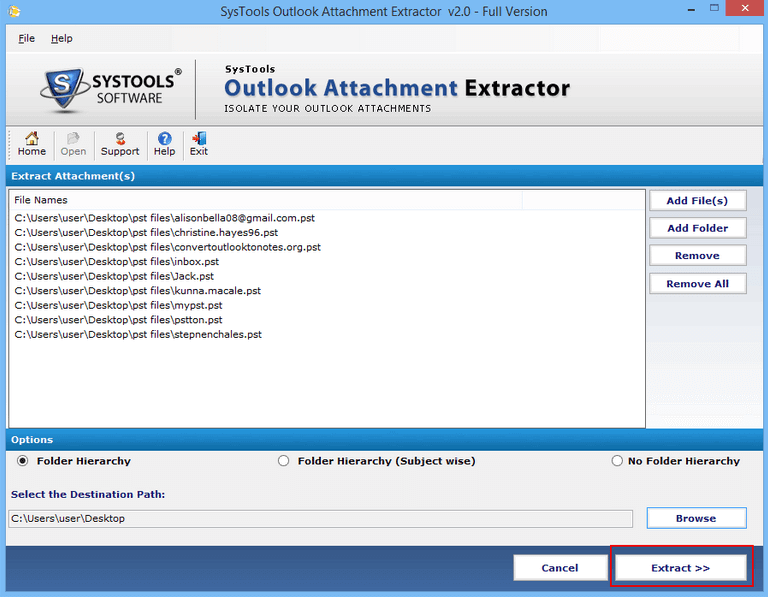
- Provide a destination location to software for saving all extracted Outlook email attachments and click on “Extract” to start the process of Outlook Attachment Extraction.
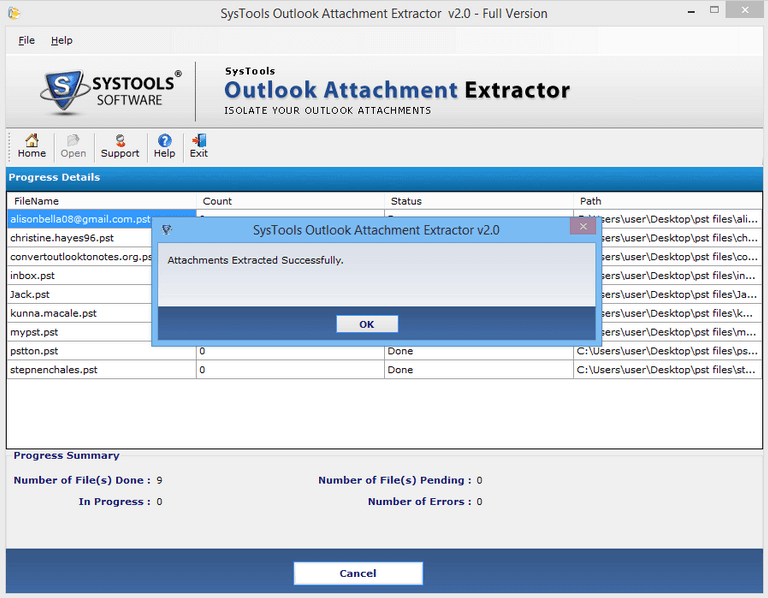
- As soon as you click on “Extract” option, the tool will provide a preview of progress summary with details like number of files and pending and errors count etc.
- On completion of the process the tool will prompt a message stating process is complete, click on “Ok” to proceed.
- Users can view the CSV log report of Outlook attachment extraction process from the destination location.
Observations Made
Positive Aspects Of Tool: The tool seems to be swift, simple and secure process of removing attachments from Outlook PST files in bulk mode. It retains metadata and formatting of emails during attachment removal process. Plus, the interface is designed by considering the needs of novice users to technical industry.
Looked Improvements:
If the provision to choose emails, files for which attachments are required, it could be beneficial for users in some way. They can choose only required files and save time to extract Outlook attachments.
Conclusion
In the bottom line of this section we can only conclude that, Outlook Attachment Extractor tool is all-in-one solution to remove attachments from any number of Outlook PST files. The tool without harming original data of PST files, extracts attachments and save them to a location of their choice in system hard drive. The tool is an affordable investment for users with advanced set of features that promise to provide assured satisfaction.