Latest Trends
Get the latest in Tech,
once a week. Free.

VR/AR
Security
Bugging Company Hardware – Legal or not? Time To Find OutMarch 5, 2026SecurityWhen you purchase something precious, like gold, jewellery, a house or something equally expensive and ostentatious, you take good care of it. You make sure that it is insured and that it is safe and protected in every way possible.
Similarly, when a business owner starts up and new business, it makes perfect sense for him to purchase new equipment of all sorts that the business would need. The business owner also hires some of the best minds in the field to ensure that the business blooms and prospers.
Learn About Spyware In These 5 Simple Points
Spyware is using software for spying over someone’s PC or devices. Once spyware is installed you can see performance of your computer drop. The main symptom
Read More
Now, it is hard to find a business owner that has spent quite some time and effort along with a significant amount of money in his business would let it all go to waste without safeguarding his property. Even from an economic standpoint it seems like an extremely foolish thing to do so.
Therefore, it makes perfect sense to a layman that a business owner or employee has installed trackers, bugs and spy application onto the office and why wouldn’t they?
It seems like quite the reasonable thing to do in light of all the ways employees exploit office hardware and internet. But, the question that stems from this is about the legality of the matter, whether employees are allowed to install trackers, bugs, spy apps on office hardware and similar equipment.
How Your PC Can Be Spied On Through Your Keyboard Keystrokes
There are times when for some reason we need to know what is going on with our PC, like what sites are being accessed or just if our keyboard keystrokes are being tracked
Read More
Is Bugging Office Hardware Even Legal?
Since business owners are the one to purchase the office equipment used by the employees in the first place, this means that employees have no ownership right over the equipment whether they bring it home with them or leave it on their office desk.
As all such equipment legally belongs to employees and business owners, they have sole ownership and responsibility of all such equipment. Therefore, they are perfectly authorized by the law to do as they please with the office equipment that falls under their ownership.
Additionally, more often than not, companies do place protective bugs and trackers on such equipment to keep track of them at all times especially if they have a mobile workforce working for them.
Monitor The Activity Of Your Windows 10 With This Keylogger
A Keylogger is an application that installs and hides in the system in order to monitor all activity that takes place in the windows operating system. Based on the
Read More
Benefits of Bugging – Bugs and Trackers
Bugs, trackers and spy applications are indeed a brilliant invention. Not only because it gives business owners more control over their work-space but also because of various other benefits it has, such as:
1. Control your Workspace
More often than not, productivity in a workspace always lags behind the expected quotient, not because the company has way more projects than it can handle but, because employees would rather spend all their time texting their co-workers, watching funny videos online or aimlessly surfing the web rather than actually doing something productive.
Such behavior not only reflects badly on the company, but it reduces the monthly revenue of a company significantly.
Spy apps and trackers can easily remedy this situation since they allow employers to keep a keen digital eye on their employees and ensure that they are doing what they are actually being paid to do.
4 Important Tips To Avoid Spyware From Disturbing You
Spyware refers to software that is installed on a computer without the user’s knowledge. It can be used to track and monitor the user activities to avoid Spyware
Read More
2. Keep Mobile Workforce in Line
Most spy apps like the TheOneSpy are equipped with both bugs and trackers. Plus, they work brilliantly if your business needs you to employee a mobile workforce.
Ever since the inception of this concept, keeping mobile workforce in line has been a hell of a task. Since they have to work onsite and away from the workspace, they tend to get countless opportunities pull wool over the employer’s eye by slacking off and taking too long to do a mental job.
With spy apps in the mix, the chances of them slacking off and running personal errands is greatly reduced since business owners can easily catch their bluff, thanks to trackers and spy apps.
3. Keep Internet Abuse at Bay
Another benefit of keeping an eye on company hardware is the millions of dollars a company can potentially save by keeping employees from having unlimited access to the internet.
Since, employees waste most of their hours at the office doing non-work related web services, it can take a serious toll on both the productivity of an employee and the monthly revenue it makes.
With the use of spy apps, business owners can not only keep track of employee’s internet usage but also reduce it significantly but limiting employee access to it.
Erase All Traces Of Your Activity In A Click & Stay Secured
One of our biggest worry is to preserve the privacy and security of our Internet browsing. This Browser cleaner Erases All Traces Of Your Activity With Just A Small Click
Read More [...]
How To Encrypt Your PC By Using Bitlocker – PC Security TipsMarch 4, 2026Security / SoftwareOne of the most powerful tools that we have today is computers. However, PCs, like it or not, are present in our daily life and most likely contain a large amount of personal information.
Information about our company or any other information that we would not want anyone to see all of it is packed into these devices (yeah, smartphones too).
Obviously, there is a need to protect all such information, for anyone who is interested in our computer shouldn’t access it.
In order to protect our files, today let’s use BitLocker, a simple tool that is provided by Microsoft. Using this tool you can encrypt all your files by just following a few steps, and then anyone without your permission can not access any of them. Cool! isn’t it?
If you do not have Bitlocker installed in your system, then you can download from the official website of Microsoft. Follow the given steps so as to encrypt your files by using Bitlocker.
Steps To Encrypt Your Information Using Bitlocker:
Step 1: Open Bitlocker
To open this application, just follow this path (Control Panel\System and Security\BitLocker Drive Encryption). Now it will open a window with different options to enable Bitlocker.
Step 2: Select The Drive
Now select the drive that you want to encrypt and click on ‘Turn on BitLocker’. For enabling this Lock, you should have the administrative privileges.
Step 3: Select The Method
Once after completing step two, it will open another window with two options, Use a password to unlock the drive and use ‘my smart card’ to unlock. Now select the first option and establish a password to unlock the drive later.
Step 4: Recovery Method
Again it will open another window where it offers several options for recovering the password that is previously entered. Select the option you want and click on continue.
Step 5: Reboot
Now you will be asked to select, how much you want to encrypt. Select the option that suits you best. Now confirm that you want to encrypt the drive by clicking on start encryption option. Once finished, simply reboot the computer.
If you have encrypted a USB, from the next time you connect it, it will ask you for the password to access the information.
As you have seen encryption of a drive is a very simple process with which undoubtedly you can improve the security of your computer. Bitlocker is a free tool that will be of great help for people who want to secure all of their files. [...]
Top 10 Ways To Protect Yourself From Cyber Crime & HacksFebruary 24, 2026SecurityFrom the start of the 21st century, the world has been experiencing a lot of changes. These changes have been faster and faster in the computer technology.
While most of these changes are improving lives, there are some which are aimed at us with evil means. In this article, we walk you through all the different measures you need to take to keep your online life safe and control cyber crime.
Here Are A Few Steps To Control Cyber Crime:
1.) Turn on your Firewall:
Most of the security software these days have the feature of ‘Firewall’. Simply turning on the firewall is going to help you a lot. Even don’t hesitate to turn on the firewall of your router. Remember it’s not being over-cautious it is being secure. It certainly helps to control cyber crime.
Network Security 101: The Evolution of Different Firewall Types
Firewalls have gone through a lot changes in the past. In this article, we show you the evolution of different firewall types which focus on the security of
Read More
2.) Use an antivirus software:
Always ensure you have good and adequate anti-virus software for your computer. The definition of viruses and bugs changes very often with people trying new ways to attack your computer.
So updating your antivirus software is equally important. Don’t forget to update your antivirus once every week.
6 Different Types Of Computer Viruses You Need To Be Careful About
To understand viruses is a very important step in protecting yourself. In this article we present to you the different types of computer viruses present and
Read More
3.) Online Shopping websites:
Do you like online shopping? I just love it. In fact, I do a lot of my shopping online. If you like online shopping as well, take care of the websites you are shopping at. I recommend you to shop only at secure websites.
Every secure Online Shopping website has a Trusted or VeriSign seal. Do put in some time to look if the website you want to shop at has these seals.
4.) Don’t give away your Credit Card details:
Never give away your personal details to websites you feel suspicious. Sharing your credit card information on the internet with people you don’t know will drag you into trouble. Be careful about where you use your credit cards information.
5.) Set up strong passwords:
Always set strong passwords for all your accounts. This could be the easiest way to avoid any major attacks. Make sure the passwords you set are not normal and difficult to guess. Include both numerical and letters in your passwords. Never use words that are very easy to guess – like your name.
Tech Trendz: 5 Technologies Fast Replacing Passwords
The best part is that these technologies are concentrating on replacing passwords with what we can consider truly unique, i.e our own
Read More
6.) Turn on your spam blocker:
Most internet providers provide a spam blocking feature to prevent unwanted messages such as fraudulent E-mails and phishing emails from getting to your inbox.
7.) By encrypting important data:
Encrypt important data you don’t want to be compromised. Use of encryption software, ” garbles ” your data to make it unintelligible to anyone who tries to hack into your computer system.
How To Encrypt Your PC By Using Bitlocker – Stay Safe
One of the most powerful tools that we have today is computers. PCs, like it or not, are present in our daily life and come with several threats. So encrypt(lock) your PC
Read More
8.) Secure your personal information:
Be wary of providing personal information via a website you know nothing about, especially those that ask for your name, mailing address, bank account numbers or any social security number.
Computer Security: How To Stay Hidden In A Computer Network
Whenever you surf the Internet, leave a piece of information that can track your activities. All this information. Here’s how you can actually avoid
Read More
9.) Beware of online scams:
Avoid getting taken in by common scams. These include foreign lotteries, on-line job frauds, phony sweepstakes and similar methods are used by cybercriminals to get your personal information and money. If it sounds too good to be true, it probably is.
How To Detect Scams, Phishing, Bots, Spam, etc?
Detect Scams easily. If you receive an email from a stranger or forwarded from a friend that seems too good to be true, what would you do? But how you can be sure? Is it really a scam?
Read More
10.) Child Security:
Monitor the online activities of your children. Make sure they only have access to computers located in central areas of your home and regularly check all browsers and email activity. Parental control software can help you limit the types of sites the user can gain access to.
Easy Way to Block Adult Sites And Content from Your Kids
There are various methods for block adult sites, Which includes modifying Parental Controls on Mac and Windows computers or even by using some browser add.
Read More
Your Thoughts
These little measures help you to a great extent to control cyber crime…. But if you feel you are hacked, don’t delay and check out this ‘article‘ to confirm and learn how to fight against it with our article on – What to do if your computer gets hacked. [...]
Web Guides
Join Our Tech Community For Free
How To
How To Completely Get Rid Of Internet Explorer From WindowsMarch 2, 2026PC HacksInternet Explorer, known as IE, is a web browser developed by Microsoft Corporation for their Operating System. It is the most widely used browser since 1999, with the highest usage (95%) in between 2002-2003.
However, its market share has gradually decreased over the years due to renewed competition from other browsers. So today we bring you an easy procedure to remove Internet Explorer from your Windows operating system completely to save you precious RAM.
Two Different Approaches To Getting Rid Of Internet Explorer
#1 Remove Internet Explorer By Using Admin Tools
This is the easiest method to remove the internet explore from your windows. For this you need to follow the path ” Control Panel> Programs> Turn Windows features on or off “.
Here, all you have to do is just uncheck the Internet Explorer that comes marked by default. To perform this task you must be using an account with administrator privileges, and also, must ensure that the browser is completely closed and there is no service that depends on it.
#2 Remove Internet Explorer By Command Console
This trick is an alternative, it is simpler than the previous one. This alternative is published on the blog of Microsoft MSDN. The steps that must be performed according to our version of Internet Explorer are:
Internet Explorer 9:
Open the command prompt by pressing ” Winkey + R ” and typing ” cmd ” in it. Once opened then just copy and paste the following statement.
Click Here To See ” How To Enable The Copy-Paste Mode In Your Command Prompt “.
FORFILES /P %WINDIR%\servicing\Packages /M Microsoft-Windows-InternetExplorer-*9.*.mum /c "cmd /c echo Uninstalling package @fname && start /w pkgmgr /up:@fname /quiet /norestart
Internet Explorer 10:
Open the command prompt by pressing ” Winkey + R ” and typing ” cmd ” in it. Once opened then just copy and paste the following statement.
FORFILES /P %WINDIR%\servicing\Packages /M Microsoft-Windows-InternetExplorer-*10.*.mum /c "cmd /c echo Uninstalling package @fname && start /w pkgmgr /up:@fname /quiet /norestart
Internet Explorer 11:
Open the command prompt by pressing ” Winkey + R ” and typing ” cmd ” in it. Once opened then just copy and paste the following statement.
FORFILES /P %WINDIR%\servicing\Packages /M Microsoft-Windows-InternetExplorer-*11.*.mum /c "cmd /c echo Uninstalling package @fname && start /w pkgmgr /up:@fname /quiet /norestart
Note: To validate these changes you must restart your computer.
In my opinion, we should not completely remove Internet Explorer as there are some web pages that are only supported by Internet Explorer.
So disabling it from the administrative tools is sufficient if you ever need the browser again. However, if you don’t want to see Internet Explorer on your system, alternatives will not miss you.
Note: You can also use the same code for any other versions just by replacing the number with the required version. So all you have to do is replace the ” M ” with the required version number like 9 or 10 or so on.
FORFILES /P %WINDIR%\servicing\Packages /M Microsoft-Windows-InternetExplorer-*M.*.mum /c "cmd /c echo Uninstalling package @fname && start /w pkgmgr /up:@fname /quiet /norestart
[...]
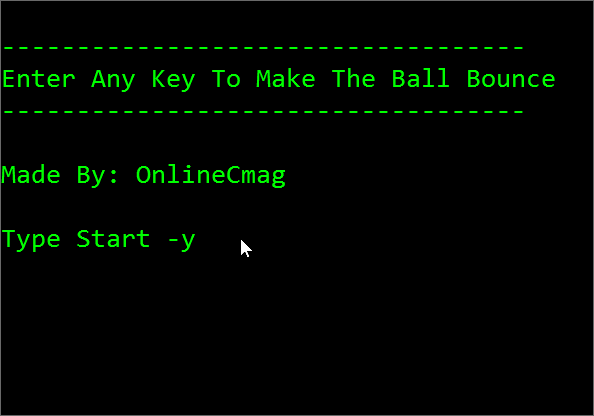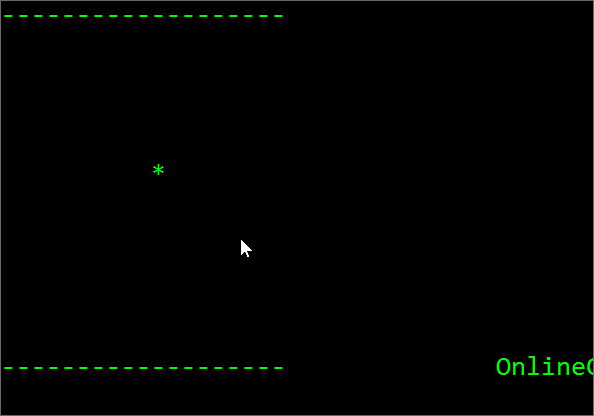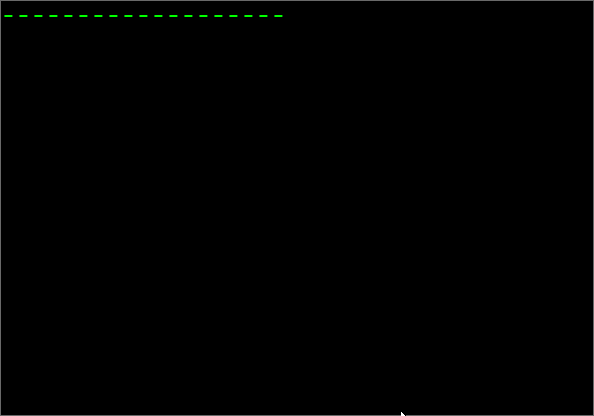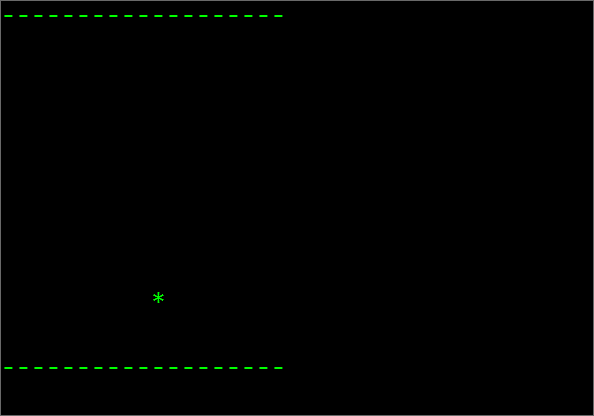
How To Create A Simple Animation Using NotepadFebruary 11, 2026Notepad TricksHello Viewers, Today we are going to show you a very interesting notepad trick to make your own animations.
Have you ever tried to design your own animation files? If not then start it know. Follow the steps below to create a simple animation.
Steps For Designing A Simple Animation Using Notepad:
Step 1: Open A New Text Document
Right-click on the desktop and select ” create a new text document ” option or just simply Open a New Text Document.
Step 2: Copy-Paste
Copy the code given below on to your notepad carefully.
Click Here To Download The Codes. Note: This download contains 3 Animations: Bouncing Ball Animation Included.
Step 3: Save The Text File
Now Save the file with a ” .bat ” extension i.e something like ” OnlineCmag.bat ”. Select the file type as ” All Files ” and encoding To ” ANSI ”.
Step 4: Run The File
Execute the file by just double clicking on it. If everything goes well you may see the following out puts.
You May Also Like
Notepad Trick To Annoy people by Constantly Repeating Messages
Ghost keyboard Typing | Make Your Notepad type Automatically
Easy Way To Create A Harmless Funny Virus with Notepad
How to Change Admin Password by Batch Programming [...]
All The Various Factors That Affect Your Computer SpeedJanuary 22, 2026System PerformanceIt’s not just about how fast your processor is or the gigs of RAM; the computer speed depends on the entire hardware with which your computer is built.
And it all comes down to how fast all the hardware exchange information amongst them and perform their tasks. So, in this article, we discuss the 8 essential factors that most likely affect your computer speed.
Also, note that your computer speed doesn’t depend solely on any one of them but on all of them collectively.
These Factors Affect Computer Speed:
#1 Processor Speed and Instruction Set
The central processing unit (CPU) is the brain of your computer and of course, the processor speed definitely matters. The speed of your CPU or processor determines how fast computers process instructions.
It is generally measured in MHz or GHz (megahertz or gigahertz). This rating actually represents the number of process cycles your CPU runs every second. A 2.6 GHz processor represents a 2.6 billion cycles per second.
But it doesn’t mean a 2.6 GHz processor is twice as fast as a 1.3 GHz processor, it boils down to the instruction set (architecture) of the processor.
Where in which the 2.6 GHz processor may require more process cycles to execute its instructions than a 1.3 GHz processor. Generally, since the information of architecture isn’t revealed it is better to go for a processor with higher clock speeds.
Examples of processor speeds and instruction sets:
Processor Speeds: 133MHz,233MHz, 350MHz, 900 MHz, 1.8 GHz, 2.6 GHz, 3.2 GHz.
Instruction Sets: 8088, 286, 386SX, 386DX,486SX, 486DX, Pentium I, Pentium MMX, Pentium II, Pentium III, Pentium 4 and so on.
#2 Bus Width and Speeds
The bus system is the communication system (a data path) that helps data transfer between the processor and the other components.
Motherboard Chipset Guide: What Is and How Chipset Works
This article will help you understand what a chipset actually means, How a chipset works and what role it plays in being a part of the motherboard
Read More
There are two such buses: The Internal Bus and The External Bus. The internal bus most commonly known as the Front Side Bus forms the network of connection between the CPU and internal components.
And the external data bus connects the peripherals (external devices like printer, scanner) to the CPU.
Examples of bus width and bus speeds:
Bus Width: 8 bit, 16 bit, 32 bit, and 64 bit.
Bus Speed: 50 MHz, 66 MHz, 75 MHz, 100 MHz, 400 MHz and 800 MHz
Bus widths may differ between the processor, memory, external slots and definitely brings in that difference to your computer speed.
#3 The Cache Memory
Cache memory is the extremely fast memory usually built into the CPU. It is similar to RAM but is more easily accessible than the normal RAM. It stores copies of frequently accessed memory locations thus reducing the time CPU takes in accessing the normal RAM.
Does Deleting the Cache Really Speed Up Your PC? – Explained
Often we worry about the speed of our computer and even try to take some serious measures to maintain and improve PC speed But can clearing Cache Actually Speed Up Your PC?
Read More
There may not be any cache memory in some processors and in some, it may range up to 2 MB. But the higher the cache memory the closer to the RAM it is.
The Level 1(L1) is extremely fast and is very low in size, L2 is fast and bigger than L1; the L3 is a little slower and the biggest among the other levels.
#4 Installing a new Operating System
Moving onto the less technical and the software corner of stuff now; a new operating system in an old computer can slow it down.
This is because the operating system takes times to adapt as it has got a huge list of files to load and make use of.
Best Lightweight Linux Distributions For Old PCs And Processors
These best lightweight Linux distributions offer countless advantages over other operating systems. Puppy Linux, Damn Small Linux, Lubuntu and the other
Read More
#5 Is your Hard Drive full?
It is commonly observed that as the hard drive is filled with data the slower it gets. It is because now the operating system has to look for the required files amongst more number of files. Also, the effect of aging on the hard drive becomes apparent.
The other way to look into this issue it the concept of fragmentation, due to which the workload of the operating system is immensely increased. However, the fact is the hard drive and hence your computer gets slower with age and usage.
#6 The Start-Up Applications:
Well, this last factor has got nothing to do with the manufacturers. Not even the best computers can perform up to the mark if there are a flood of start-up applications loading alongside the operating system.
Though you set such applications to run at startup on purpose or unknowingly, they eat up your computer’s resources and make life difficult for the operating system (particularly while loading).
6 Point Cheat Sheet To Speed Up Your Slow Computer
Is your laptop or desktop slow in processing something? Is it too slow to upload files or applications, then it’s time to speed up your slow computer follow
Read More [...]