Latest Trends
Get the latest in Tech,
once a week. Free.

VR/AR
Security
How To Know If Your Computer Has Been Hacked & Restore Control Fast!October 31, 2024SecurityHackers are basically of two different types. While Type 1 hackers use their skills to create a better world, Type 2 hackers participate in illegal activities. It is the Type 2 hackers that you have to be really careful about. Firstly, you need to acknowledge that getting hacked isn’t a myth but can happen to anyone.
If you are worried that your PC is hacked, then never delay in taking the right measures. After going through these points, in case you find similar signs on your computer, immediately head to our list of things you need to do when your computer is taken down post to restore control over your PC.
Hackers may enter your devices surprisingly, but what you need to understand is they do leave some simple signs that you can identify looking at the screen. This article will show you some possible indicators that will help you to check whether your Computer has been hacked, plus some tips for you to act fast.
Key Points To Known Whether Your Computer Has Been Hacked
Here are points which you should look for if you are suspicious about being hacked:
Point 1: Identify These Basic Signs
Consider whether something unusual is happening on your computer. You know it better than anyone and you know how it works. If it was working fine before and is stopping suddenly, it could be a sign that it is old or damaged, also there is a possibility of it being a sign that your computer is being targeted. Also if you:
1. Have standard programs and files that do not open or do not work suddenly.
2. The files that were not deleted are gone.
3. You can not access programs using your regular password. You realize that your passwords have been changed on your computer.
4. Programs on your computer that are not installed by you.
5. When you are not using the PC, but, it is often connected to the Internet.
6. The contents of the files are changed without you modifying them.
7. Your printer may not work as usual. Could not print or print different pages that you sent to print.
Point 2: Check For Accounts On The Internet
Here you could find some signs on the Internet as well if you are hacked.
1. A page or more pages will deny access because you entered the wrong password. Try to access various websites as usual; if access to the password continues to freeze, it may be because you’ve been hacked. Did you answer an email that uses the technique of “phishing” (a fake email asking you to change the security of the data or will update passwords)?
2. Internet searches are re-routed.
3. Extra browser screens may Open. These may appear or disappear without you doing anything. In addition, they could be darker or the same color, but you can see them.
4. If you purchased a domain name, you could not get it even after you paid.
Point 3: Keep An Eye For Malicious Software
Find other malicious software, replacement software, etc – that are standard elements of hackers. Other things that could happen when your computer has been hacked are:
1. False messages containing viruses. You could have anti-virus software or not, but still, if you do not, these messages of threats will alert you continuously. If you have this software know the source of this messages, that’s fine to some extent. But if these messages are from a random program you never installed, then you should be aware that these messages are false. Just do not click on them, it’s a scam to give the information of your credit card to try to get rid of viruses on your computer. Note that the hacker is already controlling your computer. See what to do next.
7 Things To Do When Your Computer Gets Hacked Without Panicing
If you’re worried that someone has hacked your computer or electronic device, then take your gut-felt concerns seriously and act fast and follow these steps
Read More
2. Additional toolbars appear in your web browser all of a sudden. You should only have one toolbar. Therefore, you should suspect if you have more than one.
3. Frequently appearing popups on your computer. You need to get rid of the program that makes these popups appear.
4. Your anti-malware program and your antivirus software does not work, or, seem disconnected. Similarly, your task manager or registry editor stops working.
5. People in your email address list will receive fake emails from your account.
6. The money from your bank account is missing or you will get the paid bills of your online shopping that you haven’t.
Point 4: Important Final Checks
If you fail to take control of any of these, consider that you’ve been hacked and things will only get worse. In particular, if the mouse cursor moves on the screen and performs actions that you do not make this surely means that someone else is manipulating your computer.
If you have given access to your work computer from another computer to fix it, then you know how it performs when used for other purposes. If this access is not authorized, then you have been hacked.
Check for your personal information leaks. Find yourself on Google. Is there any personal information online that you have not shared? This may not appear immediately but will be important to keep this in mind if you share personal information. [...]
Top 5 Tips for Maximum Windows ProtectionOctober 24, 2024SecuritySometimes it’s best to illustrate power when we put it to numbers and all we’re going to say is that at the present moment there are over 400 million users of Windows 10 alone.
The other fact that there isn’t a precise number determining how many Windows users there are in the world speaks volumes of just how popular Microsoft really is.
Chances are that you’re reading this article from your Windows operated device and if so, then you’re here to find out more about taking you Windows Protection to the next level.
There are many ways to get around protecting your Windows operating system and many of them depend on which Windows you use and how much you know about online security.
We’ll share with you five tips that can be applied to practically any Windows you have to ensure its protection.
How To Achieve Maximum Windows Protection:
1. You Need Your Backup System
One of the first things you should do to enhance your Windows protection is to have a backup plan or, to be more exact, to have a working backup system.
Prevention is the best thing you can do when it comes to your online security. Doing regular backups of your most valuable information is one way to be sure that everything crucial is kept safe at all times.
Sometimes problems don’t come from the outside but happen within your hardware and there’s no security software to keep you safe from these troubles.
There are many big name companies that offer excellent solutions for backing up your data and all you need to do is take your pick. You should also think about how you want to secure your files – an online cloud or external hard-drive?
There also a few rules to remember – have three copies of all important information on different types of backup support, make sure that the files are safe with strong passwords and set up your backups to be done automatically so that you don’t have to worry about them.
2. Antivirus Program and Firewall
You probably know that having an antivirus program is one of the first things you need to do to keep your internet security in check.
It’s quite easy to find antivirus these days, seeing that there are many strong security companies that offer their services both for free and for a fee.
All you need to do is establish what level of protection you need because free versions of antivirus programs will cover some basic security levels, but if you need more than that, you’ll have to pay to make sure your security status is good.
Also, check to see if your chosen antivirus comes with a firewall, which is a very important component of your internet shield.
If the firewall is not a part of package deal, you can always resort to Windows Firewall, which will do a decent job in protecting your OS from outside threats.
3. Against Malware and Spyware
You may need an additional level of protection against the latest forms of malware and specifically spyware, which is becoming more and more annoying with each passing year.
Changing your default browser, showing popup ads everywhere, redirecting your every search to malware riddled websites – this is the chaos that goes with spyware.
Some particularly nasty forms can even track your internet activities and use these records against you by stealing your financial details or your identity.
This is why you should also have strong anti-malware installed on your Windows and why most of us must use VPN (virtual private networks) to keep under the radar of surveillance and hacker tracking.
Believing you’ve got nothing to hide won’t save you from cybercriminals that are able to use even the smallest piece of information to disable your security systems.
4. OS and Software Should Always Be up to Date
Updates exist for a very good reason and that is to keep all the potential holes in your security patched regularly. That is why updates are fairly frequent and why you shouldn’t be irritated by them, even though they can be unwelcome.
The truth is that both your operating system and pieces of software you use should always be up to date, otherwise black-hat hackers will take full advantage of them and infect your Windows with gods know what. It would be wise to let both your system and your software update automatically so that you don’t have to handle everything manually.
It would be wise to let both your system and your software update automatically so that you don’t have to handle everything manually.
Also, take a closer look at what software you actually use and what just lingers around in your system, slowing it down unnecessarily. Whatever you don’t need, you should promptly get rid of to improve your device’s performance and security.
5. Use Your Restore Option
As soon as you install your Windows (enter number here) you should set restore point where you can have clean installation you can go back to in case something endangers your OS. This is yet another smart precaution you should
This is yet another smart precaution you should take, because this restore point will get you back to square one of your system, before any potentially problematic programs were installed. As you can see, you should always have a failsafe (or a few) to get your Windows on track faster, and you can be sure that clean installation
As you can see, you should always have a failsafe (or a few) to get your Windows on track faster, and you can be sure that clean installation restore point is going to work.
Protecting your Windows both online and offline is not a one-time thing. Security is not an exact science, which means that you will always have to work on improving it, sometimes a bit more, sometimes a bit less. The catch is never to let anything slide, if something looks suspicious, check it out, it’s better to be safe than sorry.
The catch is never to let anything slide, if something looks suspicious, check it out, it’s better to be safe than sorry.
About The Author:
Thomas Milva has been in the business of information security for four years, and strongly believes that he picked the best timing for his profession, which he often underlines in his articulate articles for wefollowtech.com. Most of the time, he works from home, and whenever he’s free, he organizes hikes for his dog, his girlfriend and himself. Tom’s home, for the time being is Baton Rouge.
[...]
Bugging Company Hardware – Legal or not? Time To Find OutOctober 22, 2024SecurityWhen you purchase something precious, like gold, jewellery, a house or something equally expensive and ostentatious, you take good care of it. You make sure that it is insured and that it is safe and protected in every way possible.
Similarly, when a business owner starts up and new business, it makes perfect sense for him to purchase new equipment of all sorts that the business would need. The business owner also hires some of the best minds in the field to ensure that the business blooms and prospers.
Learn About Spyware In These 5 Simple Points
Spyware is using software for spying over someone’s PC or devices. Once spyware is installed you can see performance of your computer drop. The main symptom
Read More
Now, it is hard to find a business owner that has spent quite some time and effort along with a significant amount of money in his business would let it all go to waste without safeguarding his property. Even from an economic standpoint it seems like an extremely foolish thing to do so.
Therefore, it makes perfect sense to a layman that a business owner or employee has installed trackers, bugs and spy application onto the office and why wouldn’t they?
It seems like quite the reasonable thing to do in light of all the ways employees exploit office hardware and internet. But, the question that stems from this is about the legality of the matter, whether employees are allowed to install trackers, bugs, spy apps on office hardware and similar equipment.
How Your PC Can Be Spied On Through Your Keyboard Keystrokes
There are times when for some reason we need to know what is going on with our PC, like what sites are being accessed or just if our keyboard keystrokes are being tracked
Read More
Is Bugging Office Hardware Even Legal?
Since business owners are the one to purchase the office equipment used by the employees in the first place, this means that employees have no ownership right over the equipment whether they bring it home with them or leave it on their office desk.
As all such equipment legally belongs to employees and business owners, they have sole ownership and responsibility of all such equipment. Therefore, they are perfectly authorized by the law to do as they please with the office equipment that falls under their ownership.
Additionally, more often than not, companies do place protective bugs and trackers on such equipment to keep track of them at all times especially if they have a mobile workforce working for them.
Monitor The Activity Of Your Windows 10 With This Keylogger
A Keylogger is an application that installs and hides in the system in order to monitor all activity that takes place in the windows operating system. Based on the
Read More
Benefits of Bugging – Bugs and Trackers
Bugs, trackers and spy applications are indeed a brilliant invention. Not only because it gives business owners more control over their work-space but also because of various other benefits it has, such as:
1. Control your Workspace
More often than not, productivity in a workspace always lags behind the expected quotient, not because the company has way more projects than it can handle but, because employees would rather spend all their time texting their co-workers, watching funny videos online or aimlessly surfing the web rather than actually doing something productive.
Such behavior not only reflects badly on the company, but it reduces the monthly revenue of a company significantly.
Spy apps and trackers can easily remedy this situation since they allow employers to keep a keen digital eye on their employees and ensure that they are doing what they are actually being paid to do.
4 Important Tips To Avoid Spyware From Disturbing You
Spyware refers to software that is installed on a computer without the user’s knowledge. It can be used to track and monitor the user activities to avoid Spyware
Read More
2. Keep Mobile Workforce in Line
Most spy apps like the TheOneSpy are equipped with both bugs and trackers. Plus, they work brilliantly if your business needs you to employee a mobile workforce.
Ever since the inception of this concept, keeping mobile workforce in line has been a hell of a task. Since they have to work onsite and away from the workspace, they tend to get countless opportunities pull wool over the employer’s eye by slacking off and taking too long to do a mental job.
With spy apps in the mix, the chances of them slacking off and running personal errands is greatly reduced since business owners can easily catch their bluff, thanks to trackers and spy apps.
3. Keep Internet Abuse at Bay
Another benefit of keeping an eye on company hardware is the millions of dollars a company can potentially save by keeping employees from having unlimited access to the internet.
Since, employees waste most of their hours at the office doing non-work related web services, it can take a serious toll on both the productivity of an employee and the monthly revenue it makes.
With the use of spy apps, business owners can not only keep track of employee’s internet usage but also reduce it significantly but limiting employee access to it.
Erase All Traces Of Your Activity In A Click & Stay Secured
One of our biggest worry is to preserve the privacy and security of our Internet browsing. This Browser cleaner Erases All Traces Of Your Activity With Just A Small Click
Read More [...]
Web Guides
Join Our Tech Community For Free
How To
Easy Way To Speed Up Windows Shutdown Time By 200%October 23, 2024PC Guides / PC Hacks / System PerformanceDoes your computer take too long to shutdown ?, If that is your problem then you arrived at right place. Today we are going to teach a simple trick that will rapidly Speed Up Windows Shutdown Time by about 200% if there is a problem in the system configuration.
If you are a regular reader at OnlineCmag then most probably you already know a lot of tricks to improve the overall performance of your computer And also various ways to shorten boot time. But it is also possible that your computer may take too long to shut down or directly get stuck in the process and you may not know why.
How To Speed Up Windows Shutdown Time
This is how you can find out what is causing problems when you turn off your computer and accelerate the Windows shutdown process.
Also See: How to Speed Up Windows 10 Boot
Disable Pagefile Deletion
Pagefile.sys is a file that Windows uses to store information about the processes that are running when the RAM is full. That is, it works as a rescue RAM. Windows has an option, normally deactivated by default, that erases all information from pagefile to shutdown a computer.
This is a measure to prevent someone with physical access to your disk storage drive from reading pagefile information. In any case, that should not be a problem if your unit is encrypted. Also when you turn off the computer, deletion of this file(pagefile) may even take several minutes.
To turn off the pagefile option while shutting down, you will have to use the Windows registry editor. Now Open the windows registry editor. Once on the registry, navigate to HKEY_LOCAL_MACHINE \ SYSTEM \ CurrentControlSet \ Control \ Session Manager \ Memory Management.
In the Memory management folder search for “ClearPageFileAtShutdown” setting. If you don’t find that file it is because Windows is not deleting the pagefile when it is finished. And if you find this file then check for the assigned value mostly it would be ‘0’. Now to stop deleting the pagefile when you turn it off simply change the value from 0 to 1.
Problems In The Event Viewer
Another way to speed up the shutdown of Windows is to find out which specific processes are slowing down the shutdown and disabling the unnecessary ones. To find the processes that are causing problems, you’ll need to use the windows event viewer. You can open it by directly searching for the event viewer in the windows search bar.
On the event viewer navigate to ” Applications And Services Logs \ Microsoft \ Windows \ Diagnostics-Performance \ Operational “. Then right – click on Operational and select “Filter Current Log …”. In the Event ID section, type 203.
Once you have filtered the errors, you will get a list with all the processes that cause problems in shutdown. Focus especially on those that mark “Error” and not “Warning”. It especially looks for those processes associated with third-party applications. Now uninstall these software if you no longer use them.
Did this trick helped you to Speed Up Windows Shutdown Time ? Did you already know these tricks? Let Us Know By Your Comments… [...]
How To Completely Get Rid Of Internet Explorer From WindowsOctober 19, 2024PC HacksInternet Explorer, known as IE, is a web browser developed by Microsoft Corporation for their Operating System. It is the most widely used browser since 1999, with the highest usage (95%) in between 2002-2003.
However, its market share has gradually decreased over the years due to renewed competition from other browsers. So today we bring you an easy procedure to remove Internet Explorer from your Windows operating system completely to save you precious RAM.
Two Different Approaches To Getting Rid Of Internet Explorer
#1 Remove Internet Explorer By Using Admin Tools
This is the easiest method to remove the internet explore from your windows. For this you need to follow the path ” Control Panel> Programs> Turn Windows features on or off “.
Here, all you have to do is just uncheck the Internet Explorer that comes marked by default. To perform this task you must be using an account with administrator privileges, and also, must ensure that the browser is completely closed and there is no service that depends on it.
#2 Remove Internet Explorer By Command Console
This trick is an alternative, it is simpler than the previous one. This alternative is published on the blog of Microsoft MSDN. The steps that must be performed according to our version of Internet Explorer are:
Internet Explorer 9:
Open the command prompt by pressing ” Winkey + R ” and typing ” cmd ” in it. Once opened then just copy and paste the following statement.
Click Here To See ” How To Enable The Copy-Paste Mode In Your Command Prompt “.
FORFILES /P %WINDIR%\servicing\Packages /M Microsoft-Windows-InternetExplorer-*9.*.mum /c "cmd /c echo Uninstalling package @fname && start /w pkgmgr /up:@fname /quiet /norestart
Internet Explorer 10:
Open the command prompt by pressing ” Winkey + R ” and typing ” cmd ” in it. Once opened then just copy and paste the following statement.
FORFILES /P %WINDIR%\servicing\Packages /M Microsoft-Windows-InternetExplorer-*10.*.mum /c "cmd /c echo Uninstalling package @fname && start /w pkgmgr /up:@fname /quiet /norestart
Internet Explorer 11:
Open the command prompt by pressing ” Winkey + R ” and typing ” cmd ” in it. Once opened then just copy and paste the following statement.
FORFILES /P %WINDIR%\servicing\Packages /M Microsoft-Windows-InternetExplorer-*11.*.mum /c "cmd /c echo Uninstalling package @fname && start /w pkgmgr /up:@fname /quiet /norestart
Note: To validate these changes you must restart your computer.
In my opinion, we should not completely remove Internet Explorer as there are some web pages that are only supported by Internet Explorer.
So disabling it from the administrative tools is sufficient if you ever need the browser again. However, if you don’t want to see Internet Explorer on your system, alternatives will not miss you.
Note: You can also use the same code for any other versions just by replacing the number with the required version. So all you have to do is replace the ” M ” with the required version number like 9 or 10 or so on.
FORFILES /P %WINDIR%\servicing\Packages /M Microsoft-Windows-InternetExplorer-*M.*.mum /c "cmd /c echo Uninstalling package @fname && start /w pkgmgr /up:@fname /quiet /norestart
[...]
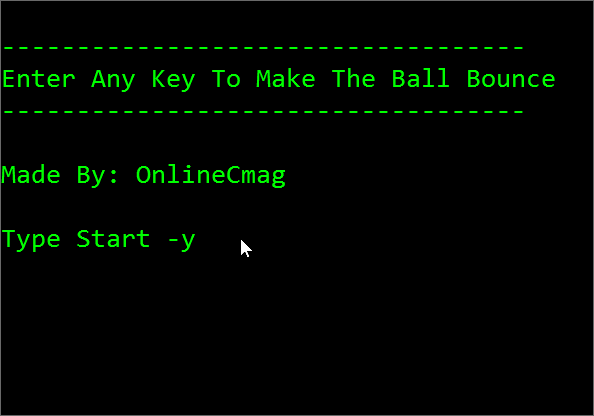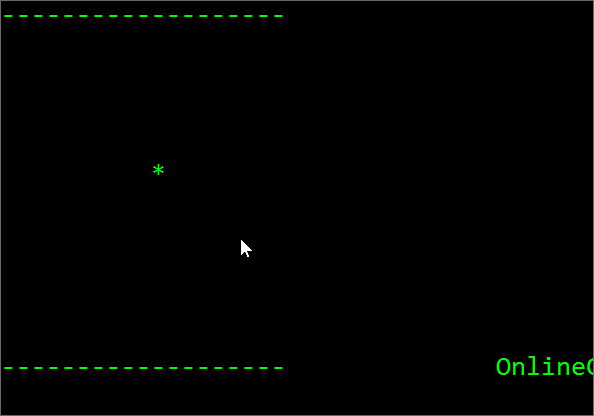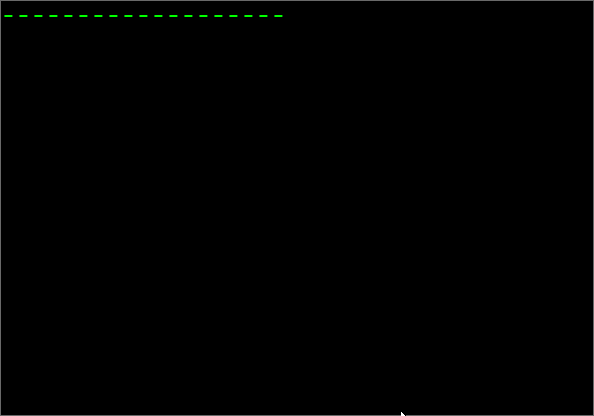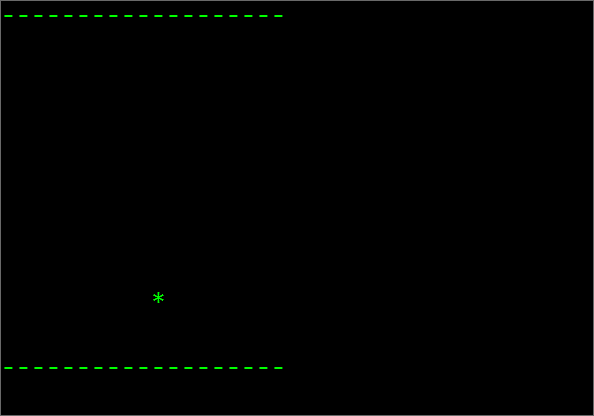
How To Create A Simple Animation Using NotepadSeptember 30, 2024Notepad TricksHello Viewers, Today we are going to show you a very interesting notepad trick to make your own animations.
Have you ever tried to design your own animation files? If not then start it know. Follow the steps below to create a simple animation.
Steps For Designing A Simple Animation Using Notepad:
Step 1: Open A New Text Document
Right-click on the desktop and select ” create a new text document ” option or just simply Open a New Text Document.
Step 2: Copy-Paste
Copy the code given below on to your notepad carefully.
Click Here To Download The Codes. Note: This download contains 3 Animations: Bouncing Ball Animation Included.
Step 3: Save The Text File
Now Save the file with a ” .bat ” extension i.e something like ” OnlineCmag.bat ”. Select the file type as ” All Files ” and encoding To ” ANSI ”.
Step 4: Run The File
Execute the file by just double clicking on it. If everything goes well you may see the following out puts.
You May Also Like
Notepad Trick To Annoy people by Constantly Repeating Messages
Ghost keyboard Typing | Make Your Notepad type Automatically
Easy Way To Create A Harmless Funny Virus with Notepad
How to Change Admin Password by Batch Programming [...]